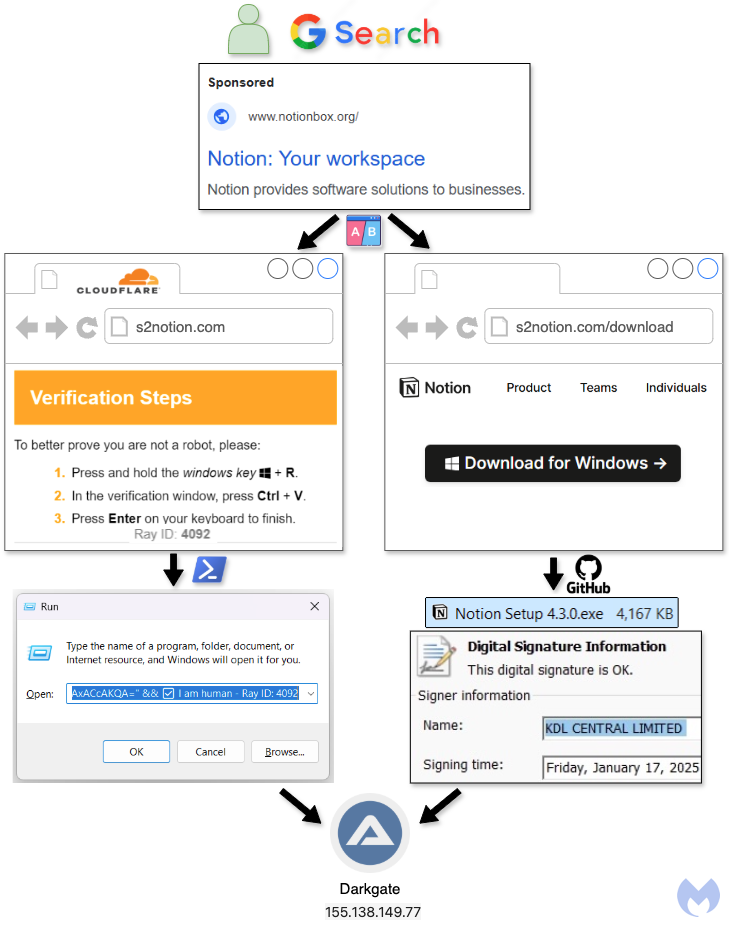
ClickFix vs. traditional download in new DarkGate campaign
During the past several months there have been numerous malware campaigns that use a technique something referred to as “ClickFix”. […]
ClickFix vs. traditional download in new DarkGate campaign Read More »