- Cisco Talos observed an increase in the number of email threats leveraging hidden text salting (also known as “poisoning”) in the second half of 2024.
- Hidden text salting is a simple yet effective technique for bypassing email parsers, confusing spam filters, and evading detection engines that rely on keywords. The idea is to include some characters into the HTML source of an email that are not visually recognizable.
- Talos observed this technique being used for various purposes, including evading brand name extraction by email parsers, confusing language detection procedures, and evading spam filters and detection engines in HTML smuggling.
Introduction to hidden text salting

Hidden text salting (or “poisoning”) is an effective technique employed by threat actors to craft emails that can evade parsers, confuse spam filters, and bypass detection systems that rely on keywords. In this approach, features of the Hypertext Markup Language (HTML) and Cascading Style Sheets (CSS) are used to include comments and irrelevant content that are not visible to the victim when the email is rendered in an email client but can impact the efficacy of parsers and detection engines.
Due to the simplicity of hidden text salting and the number of ways threat actors can insert gibberish content in emails, this approach can introduce significant challenges to email parsers, spam filters, and detection engines.
Technical explanation
Talos has observed the use of hidden text salting for multiple purposes, such as evading brand name extraction by email parsers. Below is an example of a phishing email that impersonates the Wells Fargo brand.
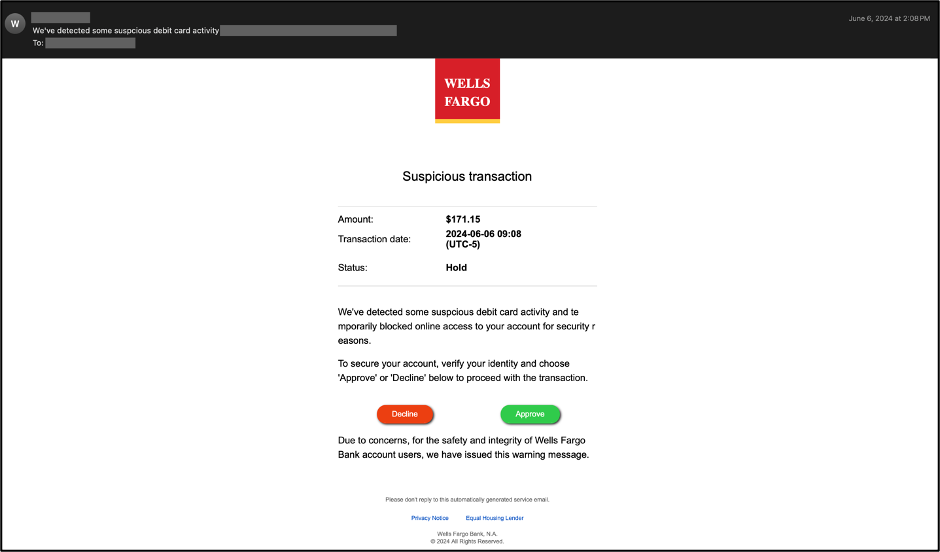
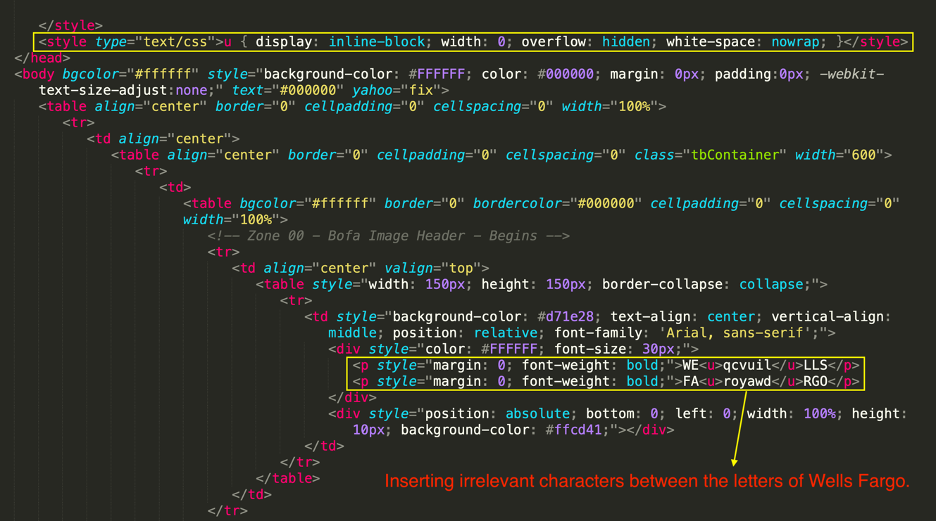
The HTML source of the above email is shown below. The <style> tag is used to define style information for an email via CSS. Inside the <style> element, one can specify how HTML elements should render in a browser or email client. The <style> element must be included inside the <head> section of the document. In this example, threat actors have set the display property to inline-block. When inline-block is used instead of inline, one can set a width and height on the element. In this case, the block’s width is set to zero. Additionally, the overflow property is set to “hidden,” resulting in the content outside the element box not being shown to the victim when the email is rendered in the email client.
As a second example, the following email shows a phishing email, sent to another customer, that impersonates the Norton LifeLock brand.
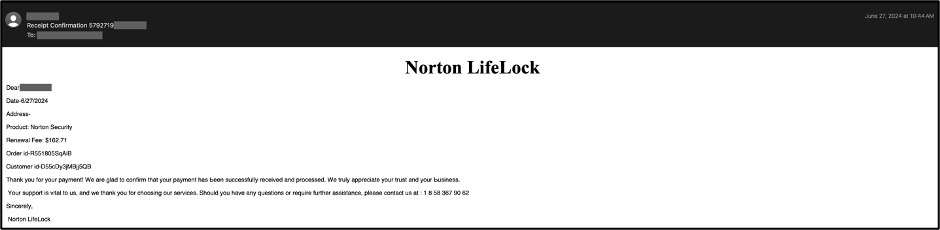
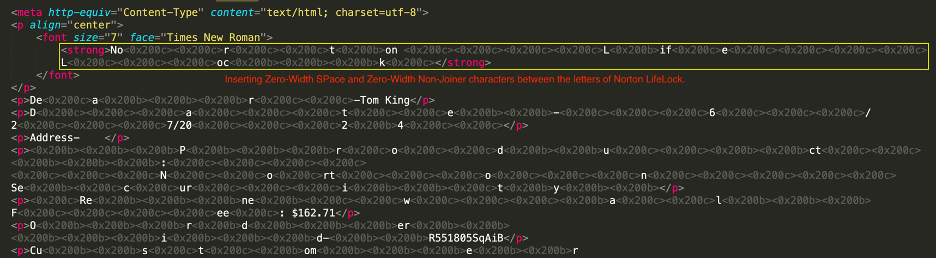
In this case, threat actors have inserted Zero-Width SPace (ZWSP) and Zero-Width Non-Joiner (ZWNJ) characters between the letters of Norton LifeLock to evade detection. Although these characters are not visible to the naked eye, they are still considered characters or strings of characters by most email parsers. Therefore, one can consider them invisible characters.
Hidden text salting has also been used to confuse language detection procedures, thus evading possible spam filters that rely on such procedures. The example below shows a phishing email that impersonates the Harbor Freight brand. As it is visually obvious, the language of this email is English.
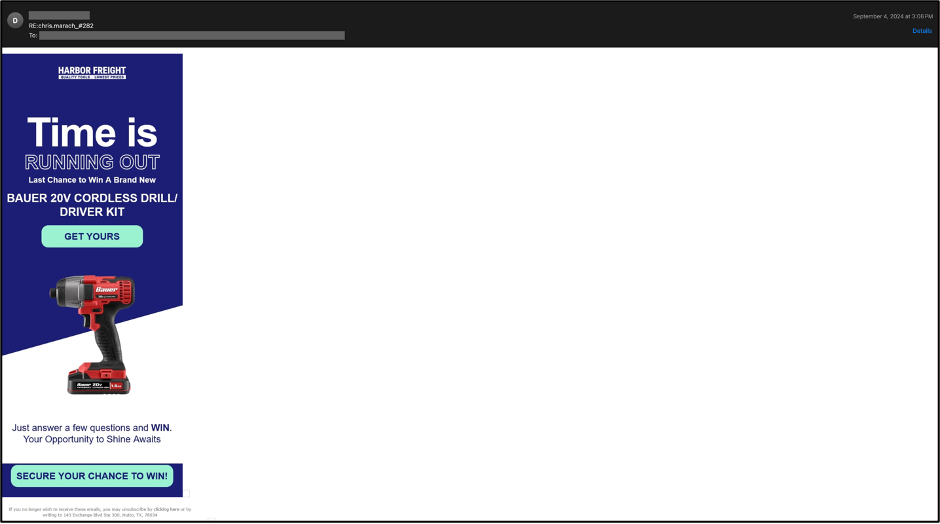
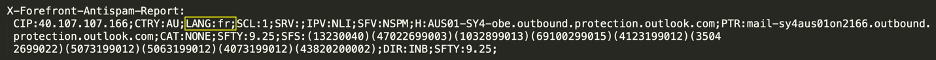
However, a closer inspection of the email’s headers shows that the language of this email has been identified as French, as it is saved in the LANG field of Microsoft’s X-Forefront-Antispam-Report anti-spam header. The LANG field specifies the language in which the message was written, and the X-Forefront-Antispam-Report header contains information about the message and how it was processed. This header is added to each message by Exchange Online Protection (EOP), Microsoft’s cloud-based filtering service.
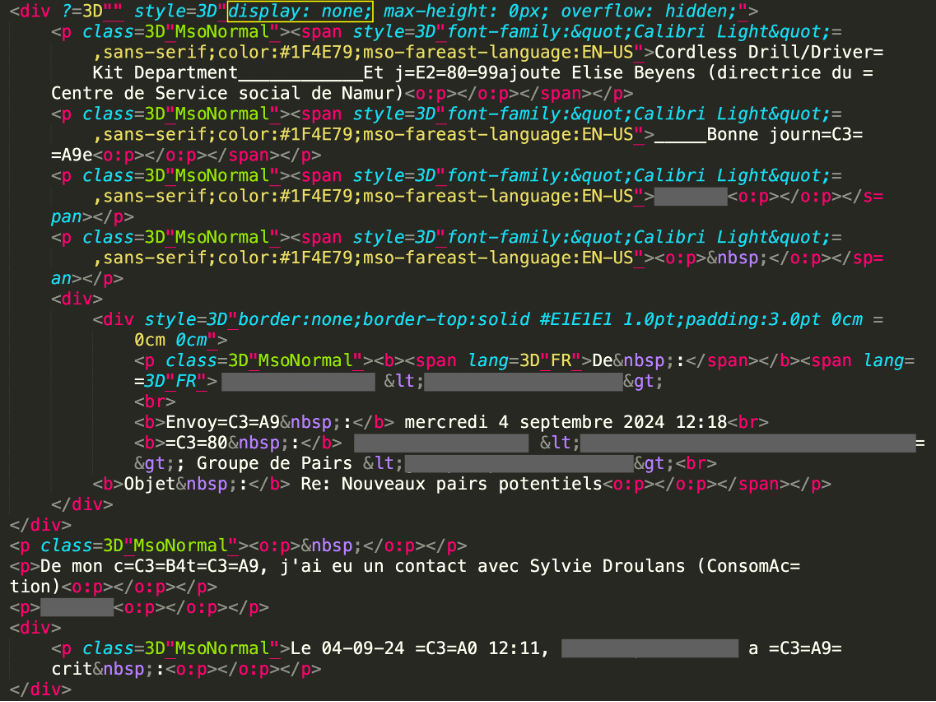
When the HTML source of this email is inspected, several French words and sentences are found that are visually hidden. In this case, threat actors have used the display property of the div element to hide the French words, thus confusing the language detection module of Microsoft.
Another case where hidden text salting has been used is in HTML smuggling in order to bypass detection engines (see the example below).

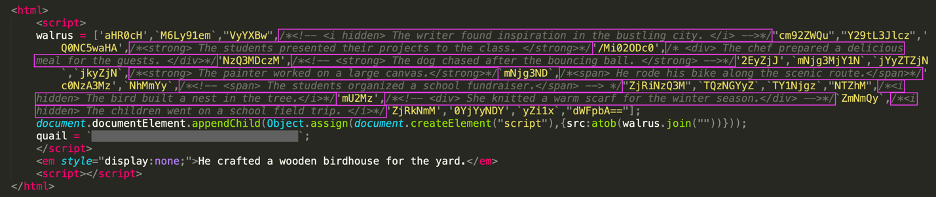
A snippet of the HTML attachment from the above email is shown below. Threat actors have inserted multiple irrelevant comments between the base64-encoded characters to prevent file attachment parsers from easily putting these strings together and decoding them.
Mitigation
The above cases are just a few examples demonstrating how simple and effective this technique is in evading detection. Detecting email content concealed through this technique, which is used to poison the HTML source of an email, is important since it poses significant challenges in identifying email threats that leverage this method. A few mitigation and detection strategies are discussed below that could be helpful in this mission.
Advanced filtering techniques: One mitigation strategy is to investigate and develop advanced filtering techniques that can more effectively detect hidden text salting and content concealment. For example, filtering systems could be made to identify questionable usage of CSS properties like visibility (e.g., “visibility: hidden”) and display (e.g., “display: none”) that are frequently used to conceal text. These systems could also examine the structure of the HTML source of emails to find the excessive use of inline styles or unusual nesting of elements that might suggest an effort to hide content.
Relying on visual features: Although improved filtering systems can be very useful in detecting hidden text salting and email threats that use this technique to avoid detection, threat actors can swiftly develop new techniques. Therefore, relying on some features in addition to the text domain, such as the visual characteristics of emails, could be helpful.
Protection
Protecting against these sophisticated and devious threats requires a comprehensive email security solution that harnesses AI powered detections. Secure Email Threat Defense utilizes unique deep and machine learning models, including Natural Language Processing, in its advanced threat detection systems that leverage multiple engines. These simultaneously evaluate different portions of an incoming email to uncover known, emerging, and targeted threats. This differentiated AI technology also extracts and analyzes the content of image-only emails that aim to evade text-based detections.
Secure Email Threat Defense identifies malicious techniques used in attacks targeting your organization, derives unparalleled context for specific business risks, provides searchable threat telemetry, and categorizes threats to understand which parts of your organization are most vulnerable to attack.
Start fortifying your environment against advanced threats. Sign up for a free trial of Email Threat Defense today.



